Get to know CyberArk. You might have nothing to lose — but your company has everything to lose.
This is a sponsored article brought to you by CyberArk.
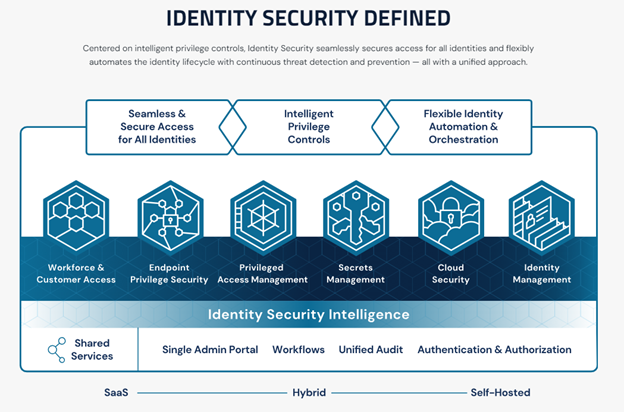
CyberArk approaches identity management differently. As a leader in both identity access and privilege access management, CyberArk can make what was once a way into the network a secured integration for everything in your cybersecurity stack.
Many organizations are finding themselves in a situation in which their products were added together in piecemeal out of urgency. In turn, these solutions are often siloed from each other — leaving them vulnerable and less likely to support major initiatives and objectives across an entire business.
These challenges speak to the importance of building an integrated Identity Security Model. This is an approach that brings together the controls found in key categories — such as Access Management and Identity Management —allowing them to complement one another.
Adaptive MFA and SSO
Validate privileged users with context-aware, adaptive multi-factor authentication (MFA) and secure access to business resources with single sign-on (SSO).
Manage Privileged Credentials
Automatically discover and onboard privileged credentials and secrets used by human and non-human identities. Centralized policy management allows administrators to set policies for password complexity, frequency of password rotations, which users may access which safes and more.
Isolate and Monitor Sessions
Maintain compliance with recorded key events and tamper-resistant audits. Establish secure, isolated remote sessions and record all activity during that session. End users never directly connect to target systems, reducing the risk of malware.
Threat Detection and Response
Automatically discover and onboard unmanaged privileged accounts and credentials. Detect anomalous behavior and indicators of compromise with policy-driven remediation capabilities.
Manage Nomadic Devices
Enforce security policies and rotate account credentials on endpoints that aren’t always connected to the enterprise network.
Endpoint Privilege Security
Take control over unmanaged privilege on endpoints to significantly reduce the attack surface and defend from threats such as ransomware.
Remote Access to PAM
Enable secure access for remote employees and external vendors to privileged access manager (PAM), no matter where they are. VPN-less, agent-less, password-less.
Endpoint Authentication
Extend multi-factor authentication to endpoints to validate and authenticate devices.
User Behavior Analytics
Use this AI-powered analytics engine to monitor the context of access requests and generate actionable insights.
For more information, contact your TD SYNNEX CyberArk team at CyberArk@tdsynnex.com