Continuously monitor and enforce compliance of all connected things with the help of Forescout.
This is a sponsored article brought to you by Forescout.
There’s no gray area when it comes to cybersecurity compliance. To hackers and regulators, partial compliance is non-compliance. Vulnerable platforms, unpatched devices and default passwords expose your network to substantial risk, creating compliance gaps that continue to widen as more devices are added or become virtual and extend into the cloud. That’s why Forescout’s mission is to continuously assess, remediate and enforce the security compliance of all devices.
Point-in-time scans, agent-only solutions and other traditional methods for maintaining device compliance are mostly ineffective. Bring your own device (BYOD), internet of things (IoT) and operational technology (OT) systems (whether on-site or off-site), as well as virtual machines and cloud instances, are dramatically expanding the volume and diversity of devices constantly accessing corporate networks. IT teams are dealing with security challenges like never before—including a rapidly growing remote workforce. To keep pace, you must be able to automate and enforce device compliance. This is where Forescout can help.
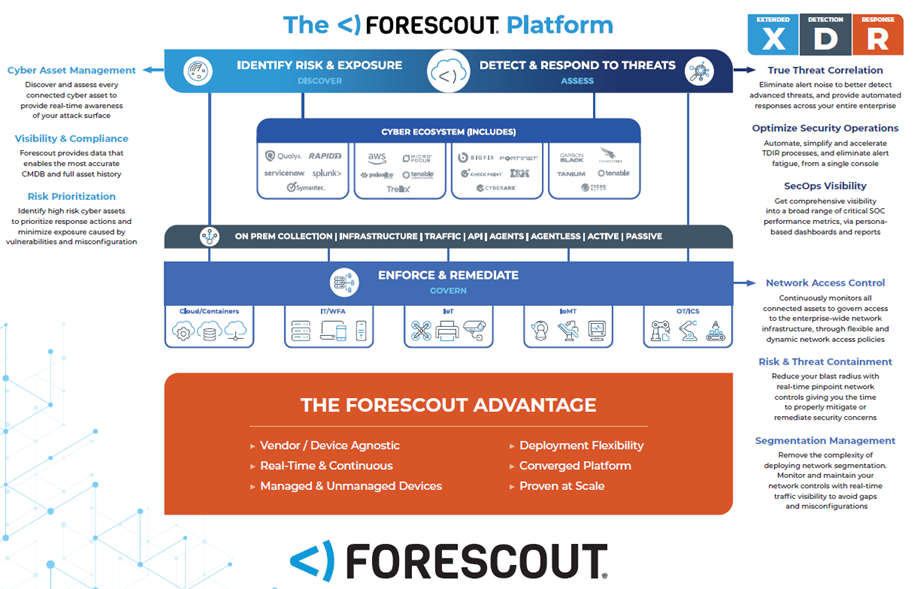
The Forescout platform delivers agentless visibility and continuous monitoring of connected devices to help you tackle these challenges. It’s simple to deploy and lets you detect and identify all IP-connected endpoints in real time—even virtual private network (VPN)-connected devices. This device visibility and control platform is the ideal solution for keeping noncompliant or unsanctioned devices off your network.
And unlike systems that simply flag violations and send alerts to IT and security staff, Forescout lets you automate and enforce policy-based network access control. Upon identifying a noncompliant device, the platform can notify users or IT staff and take immediate remediation actions, including orchestrating workflows across many of your existing security and infrastructure tools.
Regardless of device location, the Forescout platform can enforce network access control based on your policies. It continuously checks and controls device system configurations to make sure managed devices have fully functional security agents on board, all patches are current and all applications are authorized. It also manages weak or default passwords—even on IoT and OT devices.
As for BYOD and other unknown or unmanaged devices that aren’t capable of onboarding security, Forescout’s solution can passively and actively ensure that they always meet policy-based criteria or face access restrictions, including blocking, limiting or quarantining.
To learn more about the Forescout platform, contact your TD SYNNEX team at Forescout@tdsynnex.com or visit the Forescout CyberSolv page.